When its time to setup an AD password policy for your company you are going to google the process and you are going to find 1 Million ways to enforce passwords. Unfortunately most of the ways that are listed there are really geared toward older options Pre 2008 Active Directory. Most involve trying to use group policy, and are way more difficult to deploy than they need to be. And of course they never mention the gotchas, of turning on password policy in a existing environment, and then unceremoniously locking out all your users at the same time.( I mention it for a friend, Seriously it wasn’t me I don’t know what you are talking about)
Turning on Password Policy’s
If you are turning on password policy’s for users. You should be doing it with Fine Tune Password Policy’s. Its the Easiest and most flexible way to deploy password policy’s. This is because you are able to set a hierarchy and have more stringent password policy’s deploy to users.
To deploy this you will want to launch Active Directory Administrative Center(ADAC). ADAC was deployed with Server 2012/ Win 8 and makes setting up these policy’s very easy. Next go to System > Password Settings Container.
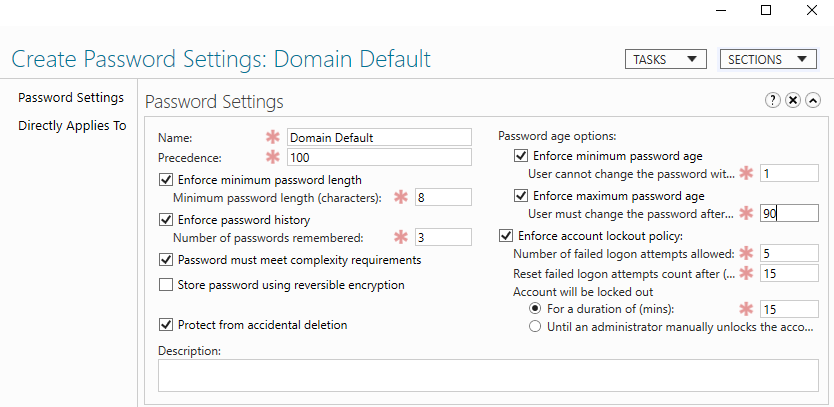
On the right hit New, Password Setting. From here you can set all of your compliance requirements and build out any precedent policy’s. For instance, I like to have Domain Admins, and Service Accounts to have more strict password policy’s. With the Domain Default applying to all domain users.
Avoiding the Gotchas
Once you have your policy created, Apply it to a test user, but not the whole Domain users group. Next we need to do some digging before applying this to a existing domain, because if you apply this to an existing account it will automatically take effect based on the last password set, not based on when this policy was applied. Meaning you can potentially lock out all your users. I didn’t actually run into this problem, mostly because my predecessors did this and then gave up on deploying passwords.
So to avoid this we need to do some digging and figure out who is going to be effected. To Find this out we will use powershell to get some ad Attributes.
get-aduser -Filter * -Properties passwordlastset, passwordneverexpires, PasswordExpired | Export-Csv "PaswordExp.csv"
This will create a spreadsheet with the list of users, and the last time there passwords were set, if there password is expired, and if they are set to manually never expire. From this we can determine who will be locked out if we are implementing a 90 day password policy, and if there are any users we need to remove password exemptions.
If you are implementing a password policy for the first time in a large company, it may be impractical to simply let users know they need to change there password. Instead you can use powershell to reset there last password date to today’s date, giving them an additional 90 day’s before there password expires. Unfortunately there is no built in way to just manually set last password date. So we have to trick the system in to resting the last set date to today. The following code, sets the password last set date to 0 then -1 which tricks it into setting it to today.
$user = get-aduser username -Properties passwordlastset, passwordneverexpires, PasswordExpired
$user.pwdLastSet = 0
Set-ADUser -Instance $user
$user.pwdLastSet = -1
Set-ADUser -Instance $user
Pulling it all together
After you have done your testing to make sure you wont lock people out you will need to apply this same process to all your users. Below is a script that looks to see if any one password was set less the 90 days ago or if they have an account the is manually set to never expire. Removes it and sets there last password date to day. Please run at your own caution and after thoroughly testing in your environment
$users = get-aduser -Filter * -Properties passwordlastset, passwordneverexpires, PasswordExpired -SearchBase "Add an OU pathe to your users so you dont apply this to service accounts"
$expirationdate = $(Get-Date).AddDays(-90)
foreach($user in $users){
if ($user.PasswordNeverExpires -eq "True" -or $user.passwordlastset -lt $expirationdate)
{
$user
$user.pwdLastSet = 0
Set-ADUser -Instance $user
$user.pwdLastSet = -1
Set-ADUser -Instance $user
get-aduser $user | Set-ADAccountControl -PasswordNeverExpires:$false
}
}
Once this is run, simply apply your password container to Domain Users and then you are set.