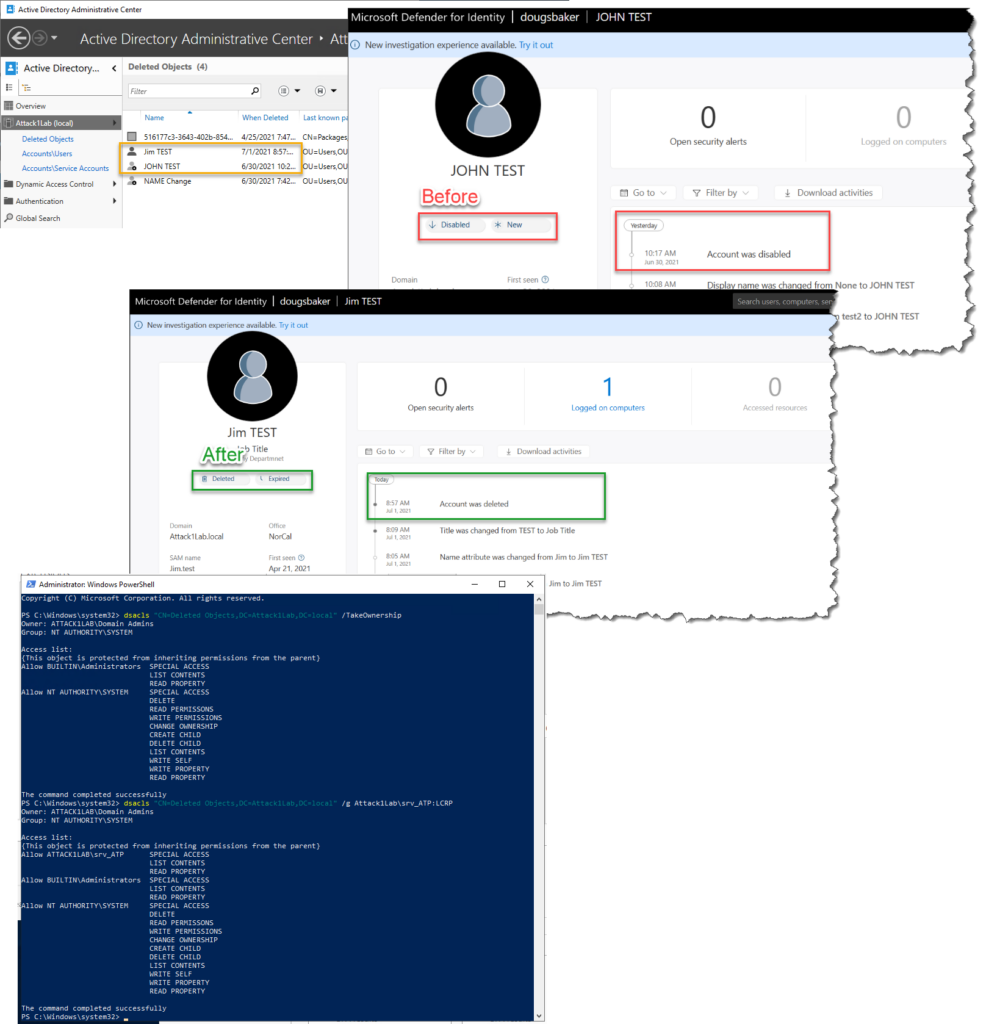
So recently I noticed in my new Server 2019 DFI lab I was not getting auditing when an object was deleted. This was curious to me as I have always in the past gotten this type of info from the product. Turns out there is one line I missed on pre-reqs that I have never run into it being an issue before.
Deleted Objects container Recommendation: User should have read-only permissions on the Deleted Objects container. Read-only permissions on this container allow Defender for Identity to detect user deletions from your Active Directory.
Microsoft Defender for Identity prerequisites | Microsoft Docs
I have always just blazed past this note because I go to the root level of the domain granted Read Acces to my service account. This works great everywhere except apparently the Deleted Objects Folder. Turns out that when you enable the Deleted Objects folder it does not by default inherit permissions. Well in this lab it the issue presented itself because I had actually gone in and enabled the AD Recycle Bin, but hadn’t done any customizations. Domain Admins had rights but no other accounts, including my Service Account. So Defender for Identity couldn’t see when an object was moved to that temp container.
You can identify if you have this issue by deleting a test AD account and wait for your portal to update. or by running the below command
#List permissions
dsacls "CN=Deleted Objects,DC=Attack1Lab,DC=local"Well if you find you have this issue don’t be too alarmed fixing it is pretty easy.
#Give yourself Permissions to modify the container
dsacls "CN=Deleted Objects,DC=Attack1Lab,DC=local" /takeownership
#Give your DFI service account access to read items in the container
dsacls "CN=Deleted Objects,DC=Attack1Lab,DC=local" /g Attack1Lab\srv_ATP:LCRP
#if using GMSA make sure you single quote the command or powershell will convert it to a variable.
dsacls "CN=Deleted Objects,DC=Attack1Lab,DC=local" /g 'Attack1Lab\gmsa-DFI$:LCRP'Hope This helps!