One of the biggest/most common misconfigurations I have seen with EOP/MDO is an overuse of IP or domain allow lists. MSFT has updated its guidelines to no longer recommend customers use those features. However, the hard thing is determining how many emails are coming into your environment without scanning due to those settings. I needed to document this the other day so I went and used the new Microsoft Security Advanced Hunting to get some stats on how big this issue was for my environment. Below are some KQL examples that might help you determine if this is an issue for your environment.
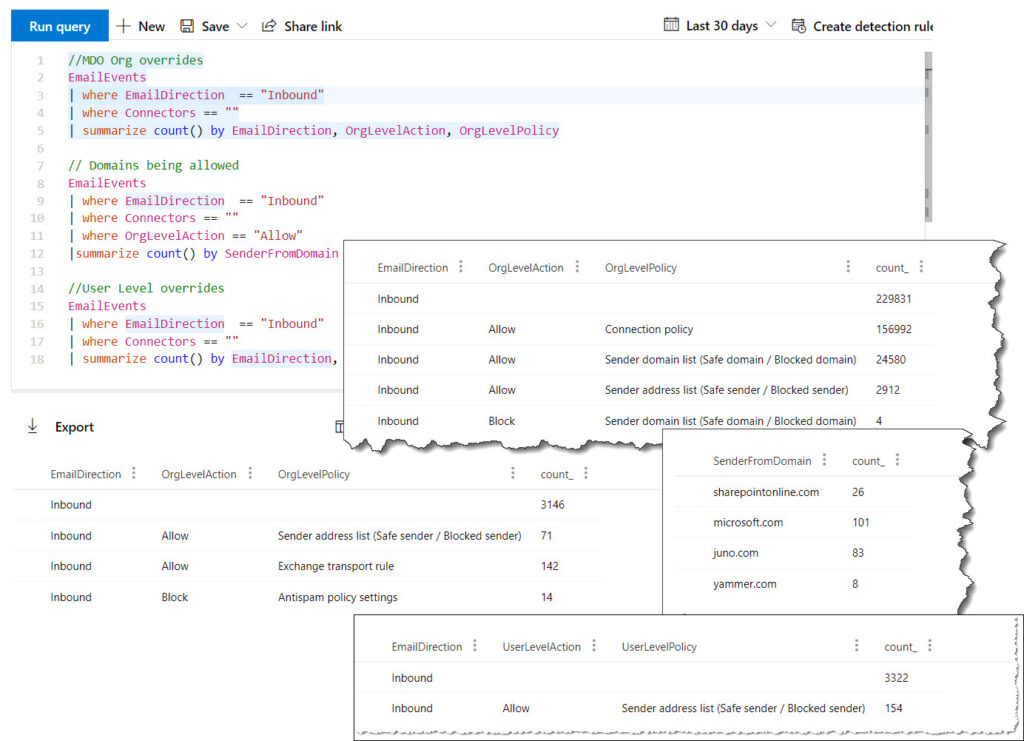
//MDO Org overrides
EmailEvents
| where EmailDirection == "Inbound"
| where Connectors == ""
| summarize count() by EmailDirection, OrgLevelAction, OrgLevelPolicy
// Domains being allowed
EmailEvents
| where EmailDirection == "Inbound"
| where Connectors == ""
| where OrgLevelAction == "Allow"
|summarize count() by SenderFromDomain
//User Level overrides
EmailEvents
| where EmailDirection == "Inbound"
| where Connectors == ""
| summarize count() by EmailDirection, UserLevelAction, UserLevelPolicy
The above KQL is assuming emails that come from a connector should not be scanned. If you need that in this report make sure you just add it in!